Massive Spying Operation Targeting Millions Of Google Chrome Users Tied to Israeli Firm
by Chris Menahan, Information Liberation:
 A massive spying operation deemed “the most far-reaching malicious Chrome store campaign to date” targeting millions of Google Chrome users has been linked to an Israeli firm, according to a report from researchers at Awake Security.
A massive spying operation deemed “the most far-reaching malicious Chrome store campaign to date” targeting millions of Google Chrome users has been linked to an Israeli firm, according to a report from researchers at Awake Security.
From Reuters, “Exclusive: Massive spying on users of Google’s Chrome shows new security weakness”:
A newly discovered spyware effort attacked users through 32 million downloads of extensions to Google’s market-leading Chrome web browser, researchers at Awake Security told Reuters, highlighting the tech industry’s failure to protect browsers as they are used more for email, payroll and other sensitive functions.
A newly discovered spyware effort attacked users through 32 million downloads of extensions to Google’s Chrome web browser, researchers at Awake Security told Reuters https://t.co/lJKesBKMxq pic.twitter.com/sKeA4H5A7f
— Reuters (@Reuters) June 18, 2020
Alphabet Inc’s (GOOGL.O) Google said it removed more than 70 of the malicious add-ons from its official Chrome Web Store after being alerted by the researchers last month.
“When we are alerted of extensions in the Web Store that violate our policies, we take action and use those incidents as training material to improve our automated and manual analyses,” Google spokesman Scott Westover told Reuters.
Most of the free extensions purported to warn users about questionable websites or convert files from one format to another. Instead, they siphoned off browsing history and data that provided credentials for access to internal business tools.
Based on the number of downloads, it was the most far-reaching malicious Chrome store campaign to date, according to Awake co-founder and chief scientist Gary Golomb.
[…] All of the domains in question, more than 15,000 linked to each other in total, were purchased from a small registrar in Israel, Galcomm, known formally as CommuniGal Communication Ltd.
Awake said Galcomm should have known what was happening.
In an email exchange, Galcomm owner Moshe Fogel told Reuters that his company had done nothing wrong.
“Galcomm is not involved, and not in complicity with any malicious activity whatsoever,”Fogel wrote. “You can say exactly the opposite, we cooperate with law enforcement and security bodies to prevent as much as we can.”
Here’s Awake’s full report and a text list of 111 malicious extension IDs.
Here’s what some of the malicious software and websites looked like:
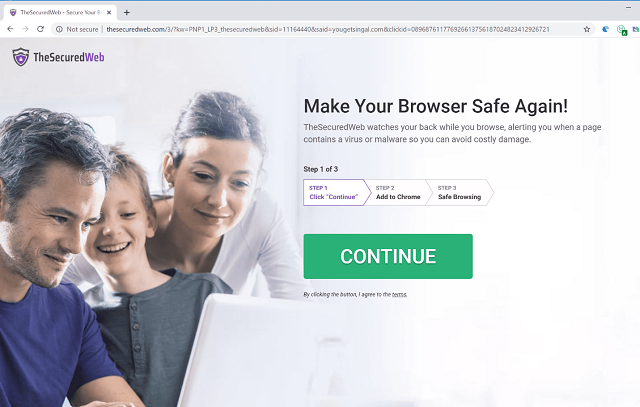
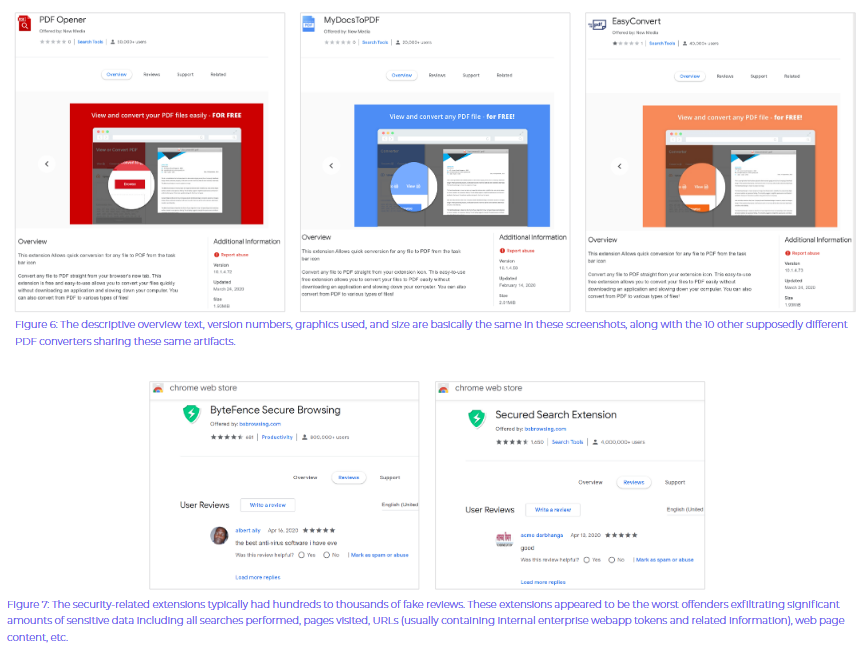
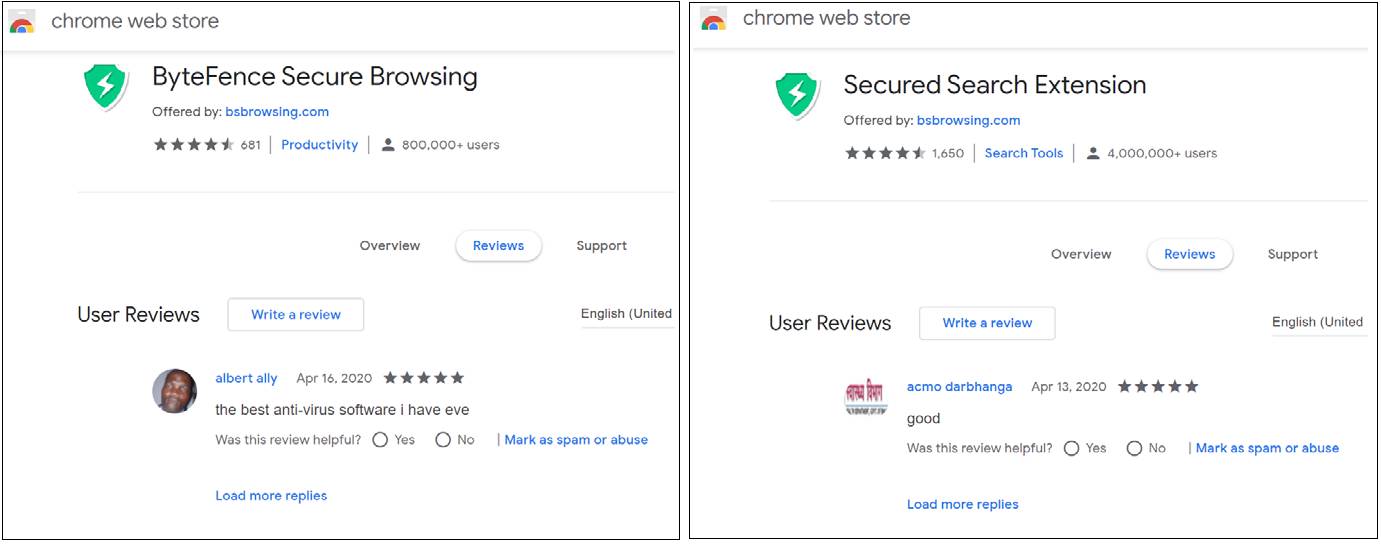
Though ICANN regularly shuts down websites for using false registration information for opsec reasons, GalComm was allowed to skirt all the rules, according to Awake.
“Throughout our research, we uncovered domains used for hosting malicious Chrome extensions, exfiltrating data, command and control, etc. All of these domains had something in common: they were all registered through a particular registrar: GalComm or Gal Communication (CommuniGal) Ltd (as shown in WHOIS). In fact, in 2019 , our threat researchers noticed that GalComm was becoming a common thread in our interactions with our customers. Since then, our analysis shows that almost 60% of the domains we have observed registered with this registrar are high risk for organizations,” Awake reported.
“[O]ur investigation found the United States Food and Drug Administration’s Office of Regulatory Affairs Health Fraud Branch (HFB) filed an abuse complaint in 2019 against GalComm for a website selling non-FDA approved abortion pills Mifepristone and Misoprostol to US consumers. While this specific complaint is not believed to be tied to nefarious activities included in this report, datapoints like this help paint a picture about the type of registrants (end users) seeking GalComm,” Awake said.
Read More @ InformationLiberation.com


